Configuring Access Level of Every Terminal in Ingress for Better Security Control of Your Premises
Introduction
Access level configuration helps clients to secure their system because they can set different Access Level for each authorized user according to the time zone. With this feature, you can limit the access of your devices to specific times and combinations of verification type in Access level, enhancing security of your premises.
Advantages
By configuring the Access Level, the security mechanism for your premises is tightened to prevent it from being invaded by any unauthorized individuals.
Process
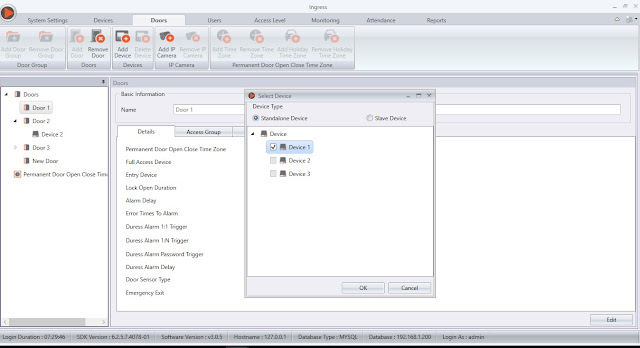
A: Configure Door Settings
Create a door in Ingress, then assign your device to that door.
Access level configuration helps clients to secure their system because they can set different Access Level for each authorized user according to the time zone. With this feature, you can limit the access of your devices to specific times and combinations of verification type in Access level, enhancing security of your premises.
Advantages
By configuring the Access Level, the security mechanism for your premises is tightened to prevent it from being invaded by any unauthorized individuals.
Process
A: Configure Door Settings
Create a door in Ingress, then assign your device to that door.
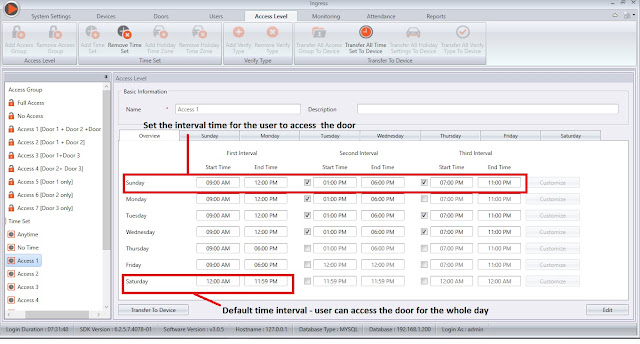
B: Configure Time Set
• Default Time Set Configuration
• Adding your own preferred Time Set
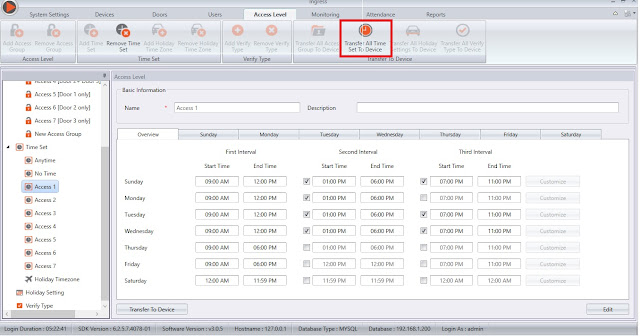
Click Add Time Set and configure the time intervals where users are allowed to access the door. Define the start and end time applicable for this Time Set. You can configure up to 3 different time sets in a day.
Click Add Time Set and configure the time intervals where users are allowed to access the door. Define the start and end time applicable for this Time Set. You can configure up to 3 different time sets in a day.
Note: User can only access the door within these 3 intervals and cannot access the door in between the break interval of these 3 time ranges.
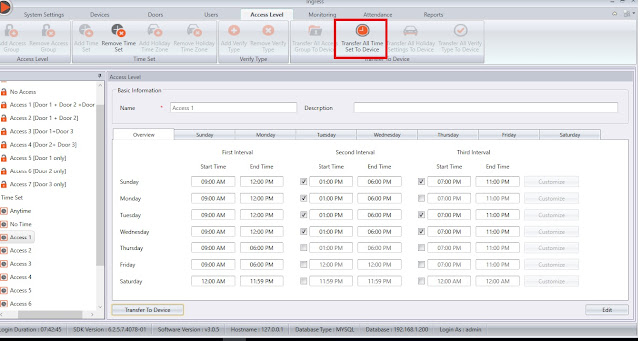
Click Save to save the settings. Once you’ve done configuring all the Time Set settings, click Transfer All Time Set to Device to synchronize all the settings to the devices.
Click Save to save the settings. Once you’ve done configuring all the Time Set settings, click Transfer All Time Set to Device to synchronize all the settings to the devices.
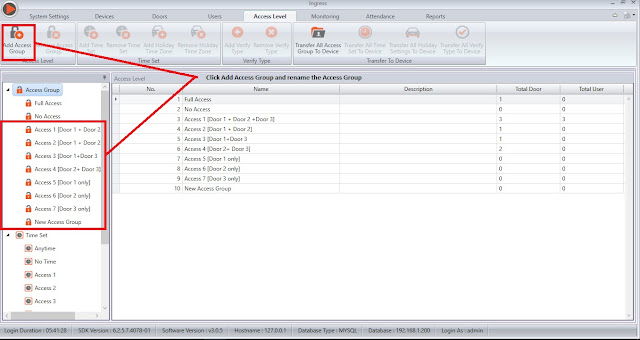
C: Configure the Access Group
As an example, for 3 terminals [3 doors], you can have up to 7 possibilities of Access groups:
1. Access 1 – Full access, can access all doors
2. Access 2 – Can access Door 1 and Door 2
3. Access 3 – Can access Door 1 and Door 3
4. Access 4 – Can access Door 2 and Door 3
5. Access 5 – Can access Door 1 only
6. Access 6 – Can access Door 2 only
7. Access 7 – Can access Door 3 only
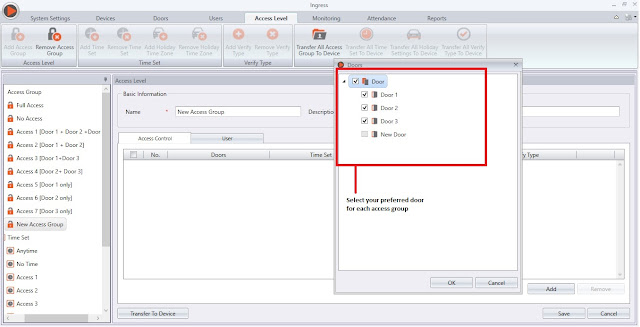
Click Add Access Door. In each Access Group, you can select your preferred Door, Time Set and Combination of Verification Type for each door.
As an example, for 3 terminals [3 doors], you can have up to 7 possibilities of Access groups:
1. Access 1 – Full access, can access all doors
2. Access 2 – Can access Door 1 and Door 2
3. Access 3 – Can access Door 1 and Door 3
4. Access 4 – Can access Door 2 and Door 3
5. Access 5 – Can access Door 1 only
6. Access 6 – Can access Door 2 only
7. Access 7 – Can access Door 3 only
Click Add Access Door. In each Access Group, you can select your preferred Door, Time Set and Combination of Verification Type for each door.
Click Save to save the settings and Click Transfer to Device to synchronize settings to the devices
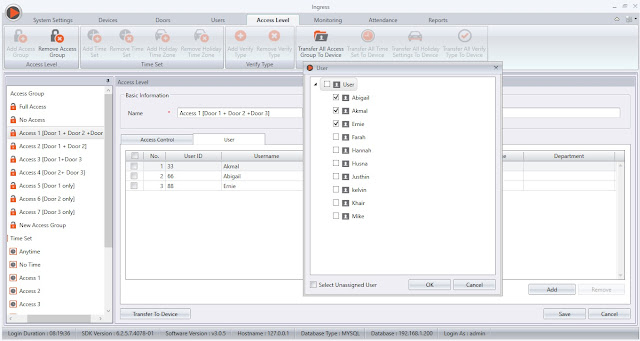
6) Once done, please assign relevant users for each access group
Access group > Edit > User > Add > Select your user > Ok > Save > Click Transfer to Device
Access group > Edit > User > Add > Select your user > Ok > Save > Click Transfer to Device
Note: Every user can only be assigned to one access group only
After the users have been added in each access group, you may select Transfer All Access Group Device to synchronize the whole settings to the device.
After the users have been added in each access group, you may select Transfer All Access Group Device to synchronize the whole settings to the device.
Related Articles
Configuring Access Level by Verify Type for a Specific Time in Ingress
Introduction In FingerTec system, Verify Type is one of the verification methods that can be used to improve access security by using a combination of verification methods. This option is readily available in most of our Access Control terminals such ...Assign User Access Level in Ingress and Synchronize to AWDMS for Smart AC1 and Face ID5 Series
Introduction The Smart AC1 and Face ID 5 series are the new facial recognition devices with options of scanning a mask or/and body temperature reading. These new devices require connection to the AWDMS before it can be connected to Ingress software. ...Navigate Ingress Better | Avoid These 5 Common Mistakes
Introduction Ingress is FingerTec’s bundled software with every purchase of FingerTec door access hardware. Over time, we have compiled common mistakes users made while using Ingress that have caused unnecessary frustration and wrong outcomes. Let’s ...Managing Employees with Multiple Time Zone Access to Multiple Doors In Ingress
Introduction In a real business operation, employees can access multiple doors within the company. To improve security, restriction of access need to be taken into great consideration. Managing access to key operational areas and restricted places is ...TC10 Access Control
Introduction TC10 is one of the devices made specifically for the TimeTec HR solution. The device previously used a 5VDC power supply, now has been changed to 12VDC which can act as a 2 in 1 device that can cater attendance record and access control ...